Lab 12-3 secure communication using ssh – In the realm of secure network communication, SSH (Secure Shell) emerges as a beacon of secure connections. Lab 12-3: Secure Communication Using SSH delves into the intricacies of SSH, unraveling its foundational concepts, configuration nuances, authentication methods, tunneling capabilities, and security considerations.
Embark on a journey to master the art of secure communication, empowering your systems and safeguarding your data.
SSH, the cornerstone of secure remote access and data transfer, establishes a robust foundation for protecting sensitive information in today’s digital landscape. With its versatility and adaptability, SSH finds applications in diverse domains, ranging from remote server management to secure web browsing.
Prepare to uncover the secrets of SSH and harness its power to elevate your cybersecurity posture.
SSH Basics
SSH (Secure Shell) is a network protocol that provides secure remote access to computer systems. It allows users to securely connect to a remote server, execute commands, and transfer files over an encrypted channel, protecting data from eavesdropping and tampering.
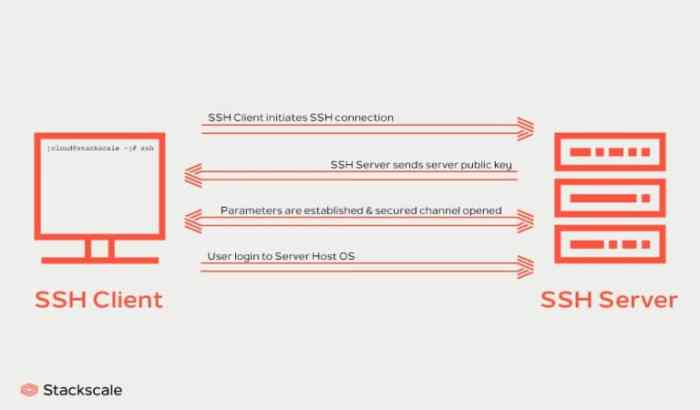
SSH establishes a secure connection through a combination of encryption algorithms, authentication mechanisms, and key exchange protocols. The SSH client initiates the connection by sending a public key to the SSH server. The server verifies the public key and sends back its own public key.
The client and server then use these public keys to generate a shared secret key, which is used to encrypt the communication channel.
Key Components of SSH Communication, Lab 12-3 secure communication using ssh
- SSH Client: Initiates the connection and sends commands to the remote server.
- SSH Server: Accepts incoming connections and executes commands from the client.
- SSH Protocols: SSH Version 1 (SSH-1) and SSH Version 2 (SSH-2) are the primary protocols used for secure communication.
- SSH Keys: Public and private key pairs are used for authentication and encryption.
Common SSH Commands
- ssh user@host: Connects to a remote server using the SSH protocol.
- scp file user@host:/path: Securely copies a file from the local computer to the remote server.
- sftp user@host:/path: Initiates a secure file transfer session.
Configuring SSH
Configuring SSH involves setting up both the SSH client and server. The SSH client configuration typically includes specifying the server address, port number, and authentication method. The SSH server configuration includes setting up the listening port, authentication mechanisms, and key management options.
Common SSH configuration options include:
SSH Client Configuration
- Host: The IP address or hostname of the remote server.
- Port: The port number used for SSH connections (default: 22).
- User: The username used to authenticate to the remote server.
- IdentityFile: The path to the private SSH key file used for authentication.
SSH Server Configuration
- Port: The port number on which the SSH server listens for incoming connections.
- ListenAddress: The IP address or hostname on which the SSH server listens for connections.
- Protocol: The SSH protocol version to be used (SSH-1 or SSH-2).
- AuthenticationMethods: The authentication methods allowed for SSH connections (e.g., password, public key).
Best practices for securing SSH configurations include:
- Use strong passwords or SSH keys for authentication.
- Disable SSH Version 1 (SSH-1) as it is less secure than SSH-2.
- Limit the number of authentication attempts to prevent brute-force attacks.
- Configure firewall rules to restrict SSH access to only trusted hosts.
SSH Authentication Methods: Lab 12-3 Secure Communication Using Ssh
SSH supports multiple authentication methods, including:
Password-Based Authentication
The most basic authentication method is using a password. However, it is less secure than other methods as passwords can be easily guessed or brute-forced.
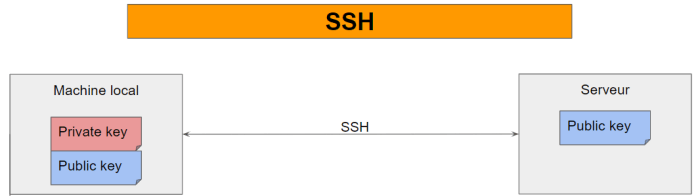
Public-Key Authentication
Public-key authentication is a more secure method that uses a pair of public and private keys. The public key is shared with the remote server, while the private key is kept secret on the client side. When the client connects to the server, the server verifies the public key and grants access if it matches.
Certificate-Based Authentication
Certificate-based authentication uses digital certificates issued by a trusted Certificate Authority (CA). The certificate contains the user’s public key and other information, such as the user’s identity and the expiration date of the certificate.
Advantages and Disadvantages of SSH Authentication Methods
| Authentication Method | Advantages | Disadvantages |
|---|---|---|
| Password-Based | Simple to set up and use | Less secure, prone to brute-force attacks |
| Public-Key | More secure, prevents password theft | Requires key management and distribution |
| Certificate-Based | Strong security, provides identity verification | Requires a trusted CA and certificate management |
Setting Up SSH Keys
To set up SSH keys, follow these steps:
- Generate an SSH key pair using the ssh-keygen command.
- Copy the public key to the remote server using the ssh-copy-id command.
- Set the permissions on the private key to 600 to protect it from unauthorized access.
SSH Tunneling
SSH tunneling is a technique that allows secure communication over an untrusted network by creating an encrypted channel through an SSH connection.
Types of SSH Tunneling
- Port Forwarding: Redirects traffic from a local port to a remote port on the server.
- Dynamic Forwarding: Allows remote hosts to connect to a local port on the client machine through the SSH connection.
Applications of SSH Tunneling
- Secure remote access to web applications
- Secure file transfer
- Bypassing network restrictions
Using SSH Tunneling
To use SSH tunneling, follow these steps:
- Establish an SSH connection to the remote server.
- Use the
- L option for local port forwarding or the
- D option for dynamic forwarding.
- Specify the local port and the remote host and port to be forwarded.
SSH Security Considerations
SSH is a secure protocol, but it is not immune to security risks. Potential risks include:
SSH Vulnerabilities
- Brute-Force Attacks: Attempting to guess the password or SSH key.
- Man-in-the-Middle Attacks: Intercepting and modifying SSH traffic.
- Phishing Attempts: Tricking users into revealing their SSH credentials.
Hardening SSH Configurations
To mitigate these risks, follow these best practices:
- Use strong passwords or SSH keys for authentication.
- Disable SSH Version 1 (SSH-1).
- Limit the number of authentication attempts.
- Configure firewall rules to restrict SSH access to trusted hosts.
- Enable SSH key logging to detect unauthorized access attempts.
SSH in Practice
SSH is widely used in various applications, including:
Remote Server Management
SSH allows secure access to remote servers for configuration, maintenance, and troubleshooting.
Secure File Transfer
SSH provides a secure channel for transferring files between local and remote systems using SFTP or SCP.
Secure Web Browsing
SSH tunneling can be used to create a secure connection to a web server, allowing users to browse the web securely over an untrusted network.
Case Study: SSH for Secure Remote Access
A company implemented SSH to provide secure remote access to its employees. The company configured SSH with strong authentication methods, disabled SSH-1, and limited the number of authentication attempts. This implementation allowed employees to securely access company resources from anywhere with an internet connection, improving productivity and reducing security risks.
Quick FAQs
What is SSH?
SSH (Secure Shell) is a network protocol that provides secure remote access to a computer over an unsecured network. It uses strong encryption and authentication mechanisms to protect the data transmitted during the session.
What are the benefits of using SSH?
SSH offers numerous benefits, including secure remote access, secure file transfer, secure command execution, and port forwarding. It also provides strong authentication mechanisms, such as public-key authentication, to prevent unauthorized access.
How do I configure SSH?
SSH configuration involves setting up the SSH server and client. The server configuration includes specifying the port number, authentication methods, and key management. The client configuration involves specifying the server’s hostname or IP address, port number, and authentication credentials.
What are the common SSH authentication methods?
SSH supports various authentication methods, including password-based authentication, public-key authentication, and certificate-based authentication. Password-based authentication is the simplest but least secure, while public-key authentication and certificate-based authentication offer stronger security.
What are the security considerations for SSH?
SSH security considerations include protecting against brute-force attacks, man-in-the-middle attacks, and phishing attempts. Implementing strong passwords, using public-key authentication, and enabling two-factor authentication can enhance SSH security.